Renesas Secure Key Installation with Free of Charge DLM Service




The increasing growth of connected devices drives the need for secure communications and secure storage. OEMs must evolve the application capability whilst keeping compatibility with legacy and existing solutions. Especially the handling of cryptographic key material is a significant challenge even at the production stage.
A secure element might seem an ideal solution; by design, it provides a very high level of physical tamper resistance (even though most applications would not demand it) and is a self-contained, isolated, and separate subsystem. But it has major weak points, though. Besides the increased cost, it is low bandwidth and a single-point-of-failure connection. The secure key storage is quite limited. The performance of the crypto accelerators is typically not documented (see references section for an independent benchmarking), few algorithms might not be supported at all, and/or not upgradeable in the field. Additional key handling tools must be integrated into the production flow or a secure programming service employed at additional cost.
The RENESAS Secure Crypto Engine (depicted in Figure 1) provides functionality comparable to a secure element with important benefits: a much higher performance, reduction of a bill of materials cost, and simpler integration of the necessary crypto functionality. It supports all state-of-the-art algorithms and a true random number generator. It enables secure and virtually unlimited key storage. The SCE subsystem is fully isolated and contained within the MCU, protected by an access management circuitry that shuts down the interface when detecting illegal access attempts. All plaintext crypto operations use dedicated internal memory, and the advanced key management capabilities avoid exposure on the internal bus fabric.

Figure 1. Secure Crypto Engine
But how to secure the factory key provisioning operations, without using a hardware security module (HSM)? All Renesas MCUs have historically supported factory programming over serial and USB interfaces, as a very reliable and low-cost mechanism suitable for mass production. The same interface can now support application key material injection.
Users can pass a chosen “installation key” and an encrypted payload (the “application key” be injected) to the SCE boundary via the built-in boot firmware, according to a documented protocol. A conceptual diagram is shown in Figure 2 below:
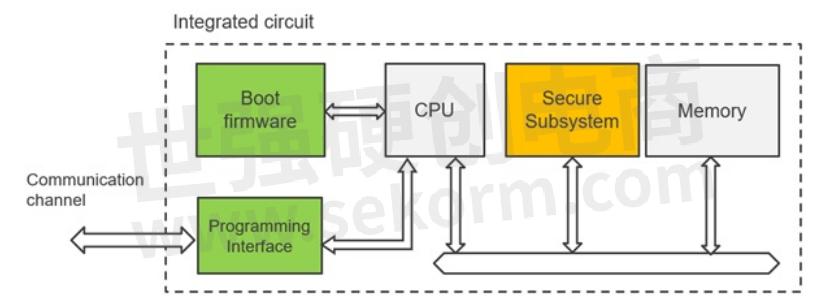
Figure 2. MCU provisioning over the programming interface
The SCE includes a Hardware Root Key (HRK), protected and unaccessible outside of its boundary. Key derivation functions are implemented to derive "key encryption keys"(KEKs, or HRK') which can transport any user key (in encrypted format) securely inside the SCE boundary for further processing. The preparation of the application key for injection is shown in Figure 3.

Figure 3. DLM server and key installation
In the first step the user chooses (generates) an AES install key (in green), and the desired application key (in yellow). The application key can be any type or size supported by the SCE engine, symmetric or asymmetric. Note: this preparation shall be done in a secure environment to preserve key confidentiality.
The application key is encrypted by the install key. Obviously, the install key shall be encrypted as well, to avoid easy interception and breach of confidentiality; and to achieve that, the HRK must be made accessible to the user. To encrypt the install key with the HRK - without exposing the HRK itself - Renesas provides a free-of-charge service to its customers. This service is delivered by a dedicated secure server (DLM server) designed to assist the MCU Device Lifecycle Management, in handling crypto keys during production and (optionally) later field updates. Any user can register free of charge to use the service, and generate the necessary data for the factory programming operation. All the communication between the user and the server is secured and encrypted via PGP.
In Figure 3, the green key 'embedded' within the blue key represents the HRK encrypted version of the user install key, which gets returned back by the DLM server. Please note that the application key (yellow) is never disclosed!
The encrypted install key can now be handled over to the SCE for decryption, and in turn, this gets used to decrypt the user key. At this point, the yellow key has been securely transported and reconstructed within the SCE boundary; now it must be saved in the MCU memory, otherwise, when power is removed, it will be lost.
To implement secure storage, the SCE implementation has another ace up its sleeve: the Hardware Unique Key (HUK). The HUK is a read-only, 256-Bit key exclusively accessible by the SCE access management circuit through a dedicated (private) bus. As for the HRK, KDFs can combine the HUK with API key generation information, and the derived keys can be used for implementing key wrapping i.e., secure key storage. The HUK itself is also stored in wrapped form in an isolated memory area (therefore, well protected from illicit access, copying, and tampering). The resulting wrapped keys can then be safely exported from the SCE boundary to be saved in non-volatile memory.
Noticeably, the installation key has no practical value outside of the factory and does not need to be stored; preparation of the installation key bundle can be performed completely "offline", and does not need an active network connection on the production site. Also, the SCE drivers provide additional APIs to use factory-installed keys for performing a "key refresh" (or key injection) in the field.
Consequently, the end application has no dependency on the DLM services during factory programming or while in the field.
This solution provides many advantages to the end user.
* Unlimited key storage, any program or data flash area available in the MCUs can be used.
* The HUK uniqueness prevents illicit cloning and copying of keys to another device.
* No need to implement a secure area on the factory floor, all keys are encrypted.
* The application keys never leave the customer's secure environment.
* No need for 'online' communication between the factory programmer and the DLM server.
* Program application and keys on the same interface, simplifying the flow.
In summary, Renesas provides a cost-effective and easy-to-use solution to help customers migrate to higher security levels in their applications. This functionality is available on the Cortex-M33-based microcontrollers of the RA6 and RA4 series.
References:
[1] Evaluation Kit for RA6M4 MCU Group
[2] R01AN5562EJ0100 Standard Boot Firmware for the RA family MCUs Based on Arm® Cortex®-M33
[3] R01UH0890EJ0110 RA6M4 Group User’s Manual: Hardware
[4] Renesas Flash Programmer (Programming GUI)
[5] Renesas Flash Programmer user manual
[6] Renesas RA Family Device Lifecycle Management Key Installation
[7] Quantitative comparison between external and internal acceleration solutions
- |
- +1 赞 0
- 收藏
- 评论 0
本文由Vicky转载自Renesas Blogs,原文标题为:Renesas secure key installation with free of charge DLM service,本站所有转载文章系出于传递更多信息之目的,且明确注明来源,不希望被转载的媒体或个人可与我们联系,我们将立即进行删除处理。
相关推荐
瑞萨RX系列MCU实现二级MCU OTA升级:FreeRTOS篇
基于空中下载技术(OTA:Over-The-Air)并通过云服务端实现的MCU固件升级得益于云供应商和设备供应商之间的合作开展,目前已具备了简单且可快速部署的集成环境。瑞萨RX云互联解决方案开发团队开始提供即便在未直接与互联网连接的二级MCU中,也可以利用AWS IoT服务方案进行OTA固件升级的示例代码。
【经验】RL78系列MCU应用技巧
全球首位的MCU供应商瑞萨,其MCU产品丰富多样。从简易的4bit到32bit各种资源,满足各行各业的需求。其中RL78系列应用最广泛。本文介绍RL78写在应用中经常碰到的问题及其解决办法。
瑞萨与野火电子达成MCU生态战略合作伙伴关系,为本土用户提供瑞萨MCU全方位的生态服务
日前,知名开源硬件供应商野火电子正式成为全球半导体解决方案供应商瑞萨电子(Renesas)MCU生态战略合作伙伴,双方将携手合作为本土用户提供瑞萨MCU全方位的生态服务,让本土用户更轻松、容易使用瑞萨MCU,加速产品开发和上市。
是否有汽车级32位MCU芯片厂家推荐?性价比如何?
瑞萨的MCU。详询世强客服
世强有没有代理NXP的安卓车载MCU
世强暂未代理NXP产品线,世强代理的瑞萨车规级32位MCU,RH850系列,具体选型资料可参考世强电商平台:RH850 Family
怎么了解中科芯mcu信息?怎么买
你好,世强代理瑞萨RA系列MCU,当前RA系列供货周期短库存丰富,可在平台直接申请样片,Renesas(瑞萨电子)RA系列Arm®Cortex®-M内核的32位MCU产品简介https://www.sekorm.com/doc/1823277.html
32位的mcu用哪个好?
32位MCU没有好不好之分,需要根据应用的具体需求选择合适的资源。世强代理的Silicon Labs和Renesas两个品牌具有32位MCU,都是有很广泛的应用市场,可靠性方面是经过时间和市场验证的。
瑞萨有8位mcu吗?
瑞萨的8位MCU属于老的78K系列,目前主推的产品是超低功耗的16位MCU RL78系列。请在世强元件电商平台搜索关键词“RL78”,便可获得相关资料。
请问世强有代理英飞凌的mcu吗?
世强目前主推的MCU产品线有Silicon Labs及RENESAS,以下是Silicon Labs的MCU选型指南,您可以点击查看:【选型】Silicon Labs(芯科科技) EFM8 8位MCU选型指南更多咨询,欢迎您随时与我们取得联系,谢谢! 服务热线:400-887-3266 服务邮箱:service@sekorm.com
世强是否代理st系列MCU?
世强代理有Silicon Labs EFM8/EFM32系列8位MCU/32位MCU,Renesas 汽车级MCU RL78 系列,RH850、V850系列,工业级MCU RX系列等。 没有ST的
世强瑞萨的MCU有哪些?详细参数
有RL78 1位的MCU产品及RX、RZ系列32位的MCU等,具体的MCU选型可以在网站上查找:https://www.sekorm.com/Web/Search/keyword/renesas%20mcu
世强有代理GD的MCU吗?
平台暂无GD MCU的供应信息。平台有Renesas和Silicon Labs的MCU详细信息,可在产品搜索。
【经验】解析瑞萨RA家族MCU的主要区别及命名规则
目前瑞萨电子(Renesas)已经发布的RA产品家族MCU主要包括四个系列即RA2系列、RA4系列和RA6系列,以及计划发布的RA8系列。有很多客户不了解RA家族处理器的主要区别和命名规则,本文讲详细讲解。
【经验】如何配置瑞萨MCU RA6T2的ADC通道
本文将介绍如何配置瑞萨(Renesas)MCU RA6T2的ADC通道,供各位工程师参考及使用。
电子商城
现货市场
服务
可定制显示屏的尺寸0.96”~15.6”,分辨率80*160~3840*2160,TN/IPS视角,支持RGB、MCU、SPI、MIPI、LVDS、HDMI接口,配套定制玻璃、背光、FPCA/PCBA。
最小起订量: 1000 提交需求>
拥有IC烧录机20余款,100余台设备,可以烧录各种封装的IC;可烧录MCU、FLASH、EMMC、NAND FLASH、EPROM等各类型芯片,支持WIFI/BT模组PCBA烧录、测试。
最小起订量: 1 提交需求>
































































































































































































登录 | 立即注册
提交评论