About BotenaGo, How can Keysight Help?




Researchers discover highly productive IOT device Botnet, known as Botenago, source code on Github. This effectively puts the power of Botenago into the hands of any unscrupulous attacker.
Over the years, there are certain historic events that become part of Security Folk Law. I'm sure you'll all recall WannaCry, NotPetya, Colonial Pipeline, and SolarWinds amongst many. And who could forget Mirai?
OK, it was 2016, so maybe a quick recap.
MIRAI
Mirai was malware that exploited vulnerabilities in millions of IOT devices, infecting them and turning them into bots, to be unwittingly used as part of extremely large botnets. Ultimately, the resulting botnets were famously used in massive DDoS attacks. In one case, the Mirai Botnet took down a key DNS service provider, Dyn, causing outages across many popular internet sites and services.
Mirai wasn't really an exploit or a hack. It was more a case of accessing publicly exposed IOT devices with inherently weak security controls, including fixed usernames and known passwords. Given the inherent insecurities traditionally built into many IOT devices, and the insane number of them out there, Mirai gave botnets a scale that had never been seen before.
One of the twists to this story is that the authors were co-founders of a DDoS mitigation solution, and so you could think of MIRAI as a key part of their business growth strategy. Another twist was that they released the code to public forums, and later to Github, in an attempt to cover their tracks. They figured they'd be safe, since they wouldn't be the only ones to have the code on their machines. However, this widespread availability was key to the botnet's overall impact, as the code was adapted to build multiple variants that targeted various architectures.
HERE WE GO AGAIN
History has a habit of repeating itself, so step forward six years, and here we go again. In November 2021, AT&T Alien Labs™ first published research on their discovery and named the malware "BotenaGo", with subtle nod to it being written in Golang (Go).
Here's what we know about BotenaGo so far:
• It's likely to affect millions of routers & IOT devices
• The code is now posted on Github
• The malware is very difficult to detect.
• One of the command and control (C2) indicators of compromise (IOCs) is from the Apache Log4Shell IOCs.
It's likely to affect Millions of Routers & IOT Devices
Best practice tells us not to expose IOT devices to the internet. Yet, given the vast range of IOT functionality, in many cases they've been designed with the expectation that they'd eventually be exposed. We also know many IOT devices have been designed with no focus on security, and in some cases utilize fixed credentials, so there really should be additional security measures deployed to protect them. Add to that the fact that BotenaGo exploits routers, and much of BotenaGo's concern is justified. You only have to run some simple searches on Shodan to find many thousands of devices that could be targeted, and that's just one search term.
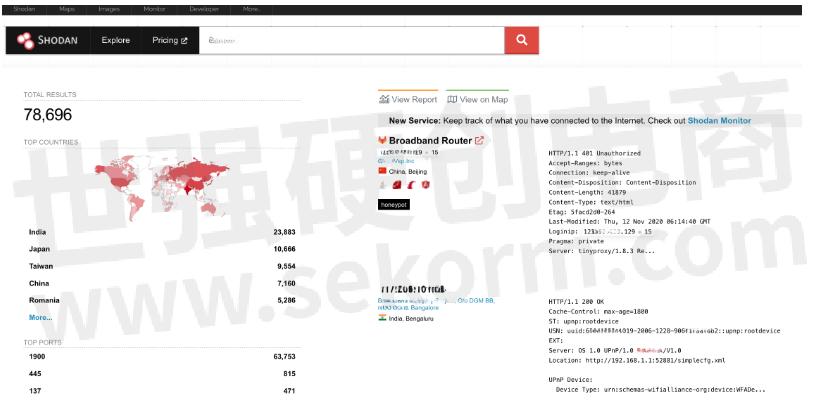
The code is now on Github
Having the code publicly available is significant. Firstly, it means that threat actors can modify the code to target additional vectors, architectures, and more. Given the language it is written in (go) is suited to ease of compilation to different architectures, it's highly likely derivatives will occur. Having access to IOT devices isn't necessarily the endgame though: we should expect this to be a pivot point for targeting other assets on the network, expansion of other exploits and architectures, and payloads. Either way, history tells us there will likely be an uptick in DDoS activity.
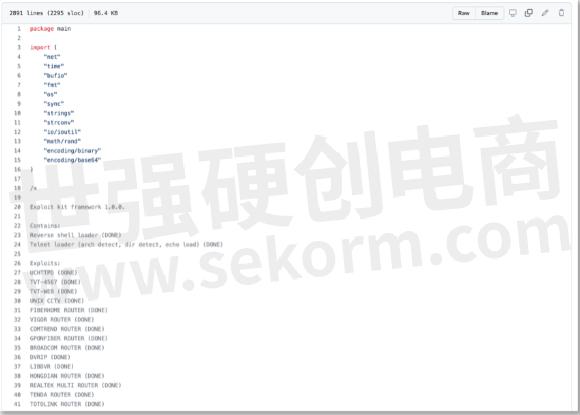
It's difficult to detect
Initially, according to VirusTotal, only 3 out of 60 security vendors detected BotenaGo. Today that's increased to 25 and no sandboxes.
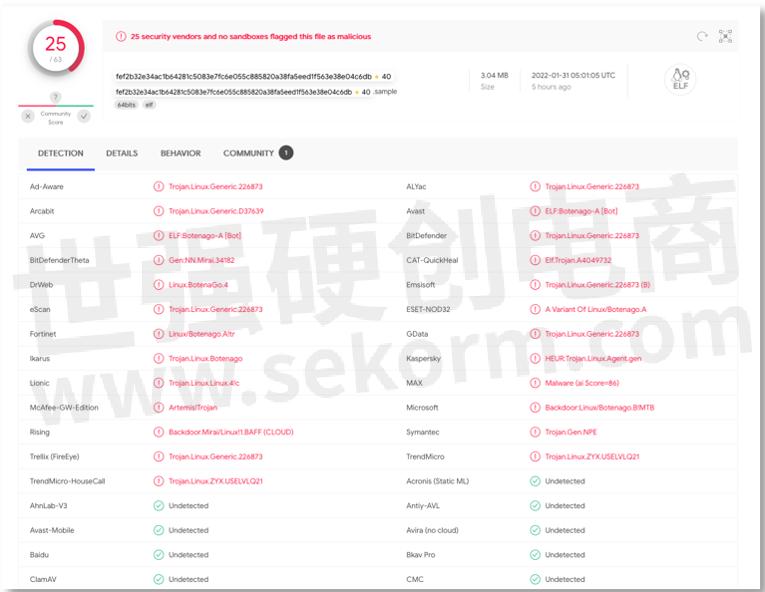
The use of Google's Open-Source Golang language (GO) is also significant, as it allows for ease of compilation for different architectures, so we should expect to see many variants as a result.
Mitigation Advice
The recommended mitigation actions haven't changed significantly from the MIRAI outbreak:
• Reduce your attack surface by minimizing IOT devices' internet exposure.
• Ensure your devices are behind correctly configured firewalls.
• Install the latest firmware and software updates.
Sage advice, for sure. However, the fact that we are seeing history repeating itself really highlights we are not addressing the problem as well as we could.
We rely on security controls, yet only 3 out of 60 of security vendors (and no sandboxes) have detected this malware.
And what about the payloads that will come from having the code on Github: will they be detected?
And how do we ensure firewalls are correctly configured?
So many questions!
How Can KEYSIGHT Help
When MIRAI first appeared back in 2016, breach and attack simulation hadn't been defined. Now you can up your game. Deploying Keysight Threat Simulator enables you to continuously measure, manage, and improve your cybersecurity effectiveness. In short, Threat Simulator helps you address these issues and many more.
Recently, our Application Threat Intelligence Team (ATI) have developed a feature on Threat Simulator called Priority Risk Mitigation. This feature gives our customers access to the latest malware of concern seen in the wild in the last 24 hours, which you'll not be surprised to hear contains BotenaGo samples.
How to know if you are vulnerable to the latest BotenaGo-based attacks
You are worried about yet another cyber threat. You hope you are protected, but you'll have to wait 4 months for your next pen test engagement to be sure. That's a long time for your network and devices to potentially be vulnerable.
Why wait? You can safely emulate a BotenaGo attack on your network right now. Just deploy a Threat Simulator agent on your network, emulate a vulnerable IOT device, and safely orchestrate an actual attack. Moreover, Threat Simulator will tell you if you were able to block the attack or not, as well as notifying you if your SIEM was alerted. Furthermore, if remediation is required, it will show you exactly how to fix the vulnerability for your specific security controls.
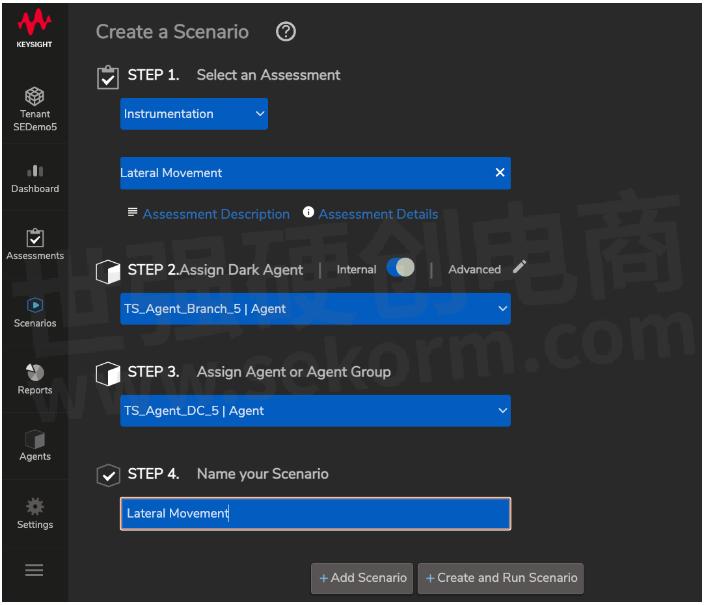
How to know if you're safe from lateral movement in the event of a successful attack
Lateral movement is a big concern. Having an IOT device compromised is one thing, but cybercriminals can cause more damage by pivoting their attack to more high-value assets, even in other network segments.
Threat Simulator enables you to be able to run full kill-chain scenarios and lateral movement with just a few mouse clicks. Deploying Threat Simulator agents in all your network segments means you can continuously run those scenarios as often as you want. And because we only target our agents, there is no risk to your high-value assets.
How to ensure you'll be able to detect new variants of BotenaGo
With so many malware variants appearing (especially in this case), coupled with a very low detection rate, you'll want to be sure you can detect any variants of BotenaGo. But how do you get the latest malware, run it through your network, and do all of that without accidentally detonating it?
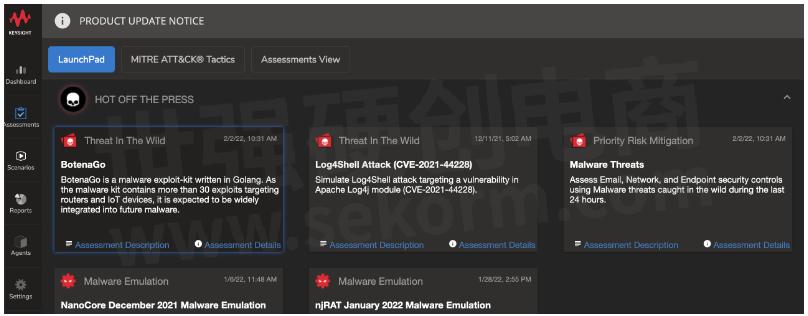
Threat Simulator has a feature we call Priority Risk Mitigation. This means we automatically notify you with the most prevalent malware we've seen in the previous 24 hours. You can then schedule assessments to test your defenses against these attacks on a daily basis. And in case you don't detect something, we'll flag that up to you so you can take immediate action. Of course, it's totally safe for your network and security tools. Although it is real malware (it would have to be to allow detection) we only target our agents, and we don't detonate it, so you are safe.
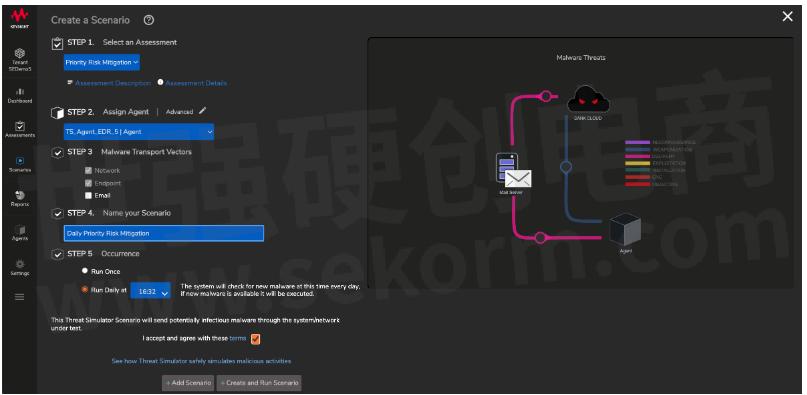
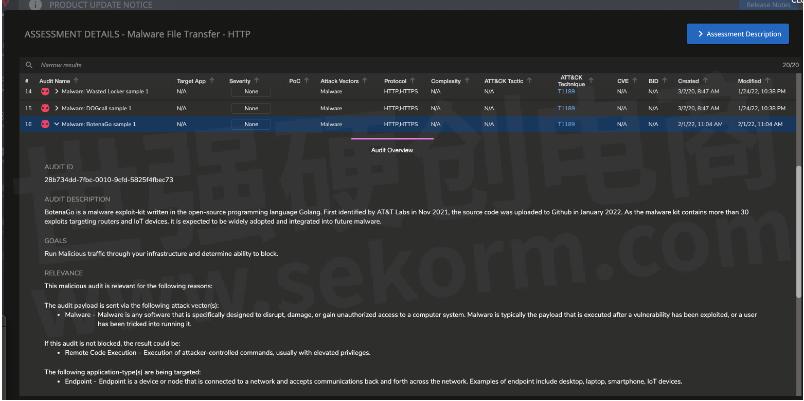
Don't go it alone
Keysight has played a leading role in security for 20 years, and Threat Simulator isn't the only way we can help you.
Concerned about IOT security? Take a look at our IOT Security Assessment Solution.
Want to test your DDoS mitigation solution? Take a look at our BreakingPoint Cloud Solution.
Want to reduce your attack Surface? Take a look at ThreatARMOR.
- |
- +1 赞 0
- 收藏
- 评论 0
本文由董慧转载自Keysight,原文标题为:Here we BotenaGo Again!,本站所有转载文章系出于传递更多信息之目的,且明确注明来源,不希望被转载的媒体或个人可与我们联系,我们将立即进行删除处理。
相关研发服务和供应服务
相关推荐
Keysight Launches Cybersecurity Partnership Program for Managed Security Service Providers, Offering an Award-winning BAS Solution
Keysight provides the proactive capabilities for MSSPs to rapidly find, remediate, and validate their customers‘ exploitable security vulnerabilities — before they become headline news.
面对物联网僵尸网络的攻击,Keysight Threat Simulator可以让您持续测量、管理和提高网络安全效率
遇到来自BotenaGo的攻击时,只需在网络上部署Keysight Threat Simulator代理,模拟易受攻击的物联网设备,并安全地策划实际攻击。此外,Threat Simulator将告诉您是否能够阻止攻击,并在SIEM收到警报时通知您。此外,如果需要修复,它将准确地向您展示如何修复特定安全控制的漏洞。
Microsoft Exchange Server EWS Insecure Deserialization, Leverage Subscription Service to Stay Ahead of Attacks
Keysight Threat Simulator or BreakingPoint products can help you assess your network security controls and determine whether you can be protected prior to patch.
What Can You Do to Strengthen Your Network?
This blog suggested a simple 3-point plan that can strengthen your network, Keysight offers many solutions that could be beneficial.
威胁模拟器系统Z2098B-171-020:20GHz射频多源机架,配备2个N5193A灵活信号源和8个N5194A矢量信号源
型号- N5194A,Z2098-60408,KS83100A,Z2098B-171-020,N5222B-417,E1135-80050,Z2098-60403,N4691D,N5194A-520,Z2098-60371,Z2098-60393,Z2098-60394,85523B,Z2098B-172-020,KS8400A,N5193A,Z2098B-222,Z2098B-104,Z2098-60437,J9150D,DSOS054A,Z2098-60436,Z2098-60435,U2002A,N5193A-520,85556A,JL253A,85530B
Z2098B V-UXG威胁模拟器源系统数据表
型号- N5194A,Z2098B,Z2098-60408,E1135-80050,Z2098B-171-4VG,Z2098-60403,N5194A-540,N5194A-520,Z2098-60002,Z2098-60371,Z2098-60393,Z2098-60010,Z2098-60394,N5193A,Z2098B-222,Z2098B-171-2V4,Z2098-60437,Z2098B-171-4V4,Z2098B-229,J9150D,Z2098-60436,Z2098-60435,Z2098B-171-2VC,Z2098B-171-4VC,Z2098B-171-2VG,Z2098B-171-2V8,N5193A-540,Z2098B-171-4V8,N5193A-520,JL253A,Z2098B-242
网络性能和安全产品目录
描述- 本资料主要介绍了Keysight公司提供的网络性能和安全产品,包括威胁模拟器(Threat Simulator)、威胁ARMOR、Hawkeye和SSL VPN网关评估服务。这些产品旨在帮助用户识别和修复安全漏洞,提高网络安全性,并确保网络性能。资料详细介绍了每个产品的功能、部署方式、许可证类型以及如何通过这些工具来增强网络安全和性能监控。
Threat Simulator ——入侵与攻击模拟
型号- 983-2012,983-2111,983-2133,983-2013,983-2112,983-1012,983-2014,983-2113,983-2114,983-2015,983-2115,983-22014,983-2019,983-2020,983-2010,983-2131,983-2011,983-2110,983-101
Keysight’s on-premises solutions as well as cloud-based solutions in RSA 2022
At the Keysight booth, we were showing off our on-premises solutions as well as our cloud-based solutions. These solutions included: Flex taps and iBypass switches, inline and out-of-band Vision ONE network packet brokers, Threat Simulator, and CyPerf.
威胁模拟器系统
型号- Z2098-60408,KS83100A,U2022XA,E1135-80050,Z2098-60403,Z2098B-172-408,Z2098B-171-408,Z2098-60371,Z2098-60394,M9807A-200,85523B,KS8400A,N5193A,Z2098B-244,Z2098B-104,J9150D,Z2098-60434,DSOS054A,M9019A,N4692D,N5193A-540,85556A,JL253A,85540A,Z2098B-242
A-UXG威胁模拟器源系统
型号- Z2098B-172-208,Z2098-60408,Z2098B-172-404,Z2098B-172-204,E1135-80050,Z2098-60004,Z2098-60403,Z2098-60006,Z2098B-172-408,Z2098-60002,Z2098B-171-408,Z2098-60371,Z2098B-171-X04,Z2098-60010,Z2098-60394,Z2098B-171-X08,Z2098B-171-204,Z2098B-171-404,Z2098B-171-208,N5193A,Z2098B-222,Z2098B-244,Z2098B-224,Z2098-60437,Z2098B-229,J9150D,N5193A-540,N5193A-520,JL253A,Z2098B-242
Z2098B UXG威胁模拟器校准系统
型号- Z2098B,Z2098B-172-208,Z2098B-172-404,Z2098B-172-204,Z2098B-171-4VG,Z2098B-172-X0X,Z2098B-172-408,Z2098B-171-408,Z2098B-172-4VG,Z2098B-172-2VG,Z2098B-171-204,Z2098B-171-404,Z2098B-171-208,Z2098B-172-XVX,Z2098B-171-2V4,Z2098B-172-4V8,Z2098B-171-4V4,Z2098B-172-2V8,Z2098B-172-4VC,Z2098B-172-2VC,Z2098B-171-2VC,Z2098B-171-4VC,Z2098B-171-2VG,Z2098B-171-2V8,Z2098B-172-4V4,Z2098B-171-4V8,Z2098B-172-2V4
现货市场
服务
提供是德(Keysight),罗德(R&S)测试测量仪器租赁服务,包括网络分析仪、无线通讯综测仪、信号发生器、频谱分析仪、信号分析仪、电源等仪器租赁服务;租赁费用按月计算,租赁价格按仪器配置而定。
提交需求>
朗能泛亚提供是德(Keysight),罗德(R&S)等品牌的测试测量仪器维修服务,包括网络分析仪、无线通讯综测仪、信号发生器、频谱分析仪、信号分析仪、电源等仪器维修,支持一台仪器即可维修。
提交需求>































































































































































































登录 | 立即注册
提交评论