Harnessing the Power of IoT Security Assessment Tool Plugins




The KEYSIGHT IoT Security Assessment platform is a powerful suite of tools for testing many different types of IoT devices and protocols. Out of the box, it can fuzz Bluetooth, WIFI, and Ethernet at the protocol level, as well as hundreds of specific assessments targeting just about any type of device communication method you could think of including CAN bus and cellular. However, even with all the built-in functionality, it is impossible to cover every aspect of the IoT ecosystem, which is why the IoT Security Assessment Tool was designed to be quickly and easily extended with custom plugins. Through the use of plugins, you can leverage your own existing scripts and test harnesses, add coverage for unique devices, and generally make the IoT Security Assessment Tool work in any custom environment.
Anatomy of a Plugin
Under the hood, plugins for the IoT Security Assessment Tool are essentially just tar archives that contain a few boiler-plate script files, a config file, and a docker image. The purpose of these files can be briefly summarized as:
· Script files – These contain generic instructions for installing and registering the plugin within the system. There is also a script for defining how to run the included docker image file if needed. These do not vary from plugin to plugin except for changing a named reference here or there, and I would not be surprised if these were moved out of the individual plugins in the future in favor of universal scripts run from the backend system instead.
· Config file – This is a json file used to define how the plugin appears in the UI and any underlying system dependencies. This is also, more importantly, where you define the audits included in the plugin. The audit definitions contain all the declarations of variables used for interacting with your test scripts inside the docker image as well as what communication protocol the audit will use.
· Docker image – This is a docker image saved as a .tar.gz file. As with any docker image, this can be pretty much whatever you need it to be. You build your docker image with a Dockerfile just like normal but with the one caveat that you need a special `runner.py` file as the ENTRYPOINT to interact with the backend and get access to the variables defined in the config file. From there you are free to call out to any other script or binary you would like. Once you have your docker image created, you save it using `docker save` and gzip compress it for inclusion in the plugin archive.
And that is all that is needed to create your custom plugin to extend the functionality of the IoT Security Assessment Tool. Now let’s take a look at an example.
Recreating a Bluetooth Prank from DEFCON 31
If you were at DEFCON 31 earlier this year and made the unfortunate mistake of neglecting to disable Bluetooth on your iPhone while walking around the conference, you may have been treated to an interesting dialog pop-up:

Of course, there was no Apple TV in the area, and if you had, against your better judgment, clicked on the Continue button in the dialog, it wouldn’t have done anything. What was happening was someone on the conference floor was blasting out specific types of BLE advertisement messages. These advertisements spoofed certain accessories or actions that would be recognized by Apple devices and caused them to display messages like the one pictured above. It was just the advertisement beacon and nothing else, so there was nothing malicious about it. It was simply some DEFCON hijinks that spread awareness about this Apple “proximity pairing” functionality and also served as a nice reminder to turn your Bluetooth off. It also happens to be a perfect way to show what a custom IoT Security Assessment Tool plugin is capable of.
Thanks to the work done by ECTO-1A and others, we have a fairly extensive list of BLE advertisement messages that will trigger the proximity pairing response. Using this information, I wrote a Python script that will take a given message and call it out to the `hcitool` BLE linux utility to send out the beacon on one of our supported Bluetooth dongles, specifically the LM1010. I used this script as my `runner.py` and set it to the ENTRYPOINT of a docker image based on python:3.9-slim, making sure to install any extra packages needed for the hcitool utility such as bluetooth, blues, rfkill, etc. In my config file, I defined a drop-down list variable of all the different types of accessory beacons that correlated with my Python script. I also specified that this module would be using the LM1010 as its interface. Once my docker image was built and saved as a .tar.gz archive, I combined it with my config file and the other installer scripts and packaged the entire thing up as a tar archive with a .pkg.tar file extension. Now that it was ready for installation, there was one other small caveat to take care of first. On the file system of the IoT Security Assessment Tool, there is a json file that keeps track of module compatibility. For my plugin module to be seen as compatible with the current version of the tool, I had to add an entry to the bottom of the `/srv/pentestsw/config/compatibility_db.json` file using the name of my plugin and the build number, a value chosen by me (by convention this is usually a timestamp of when the plugin was built) and declared in the config file from earlier. Once all of this was done, the plugin package I created was able to be installed and all of the audits I had defined showed up seamlessly in the UI, appearing just like all the built-in functions.
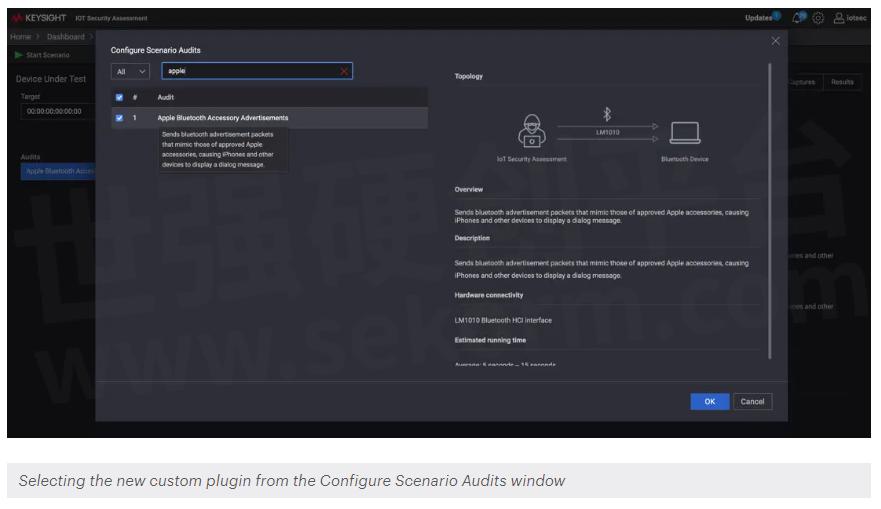
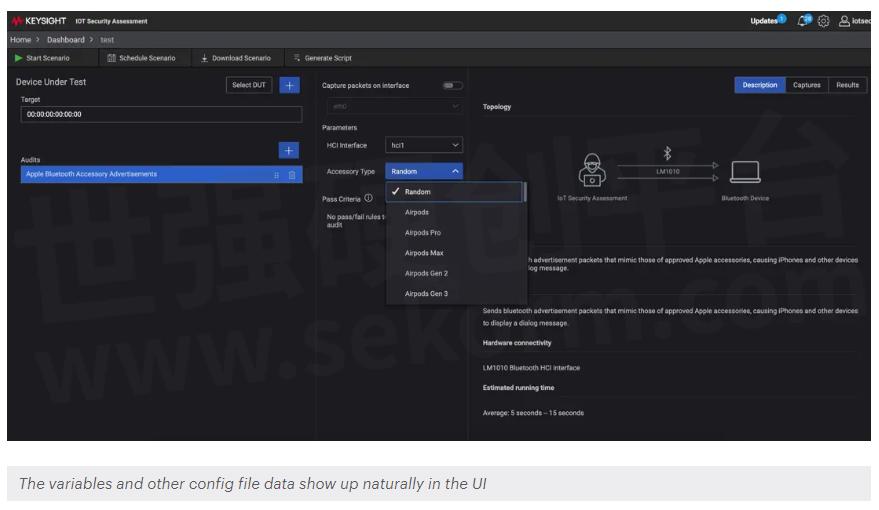
The end result of running the new test looks like this:

As you can see, the ability to write custom plugins for the IoT Security Assessment Tool makes the possibilities endless. You can pull in your existing test tools and scripts, write new ones that make use of our tool’s infrastructure, and generally make the IoT Security Assessment Tool a seamless addition to any IoT testing environment.
- |
- +1 赞 0
- 收藏
- 评论 0
本文由雪飘梦飞转载自Keysight Blogs,原文标题为:Harnessing the Power of IoT Security Assessment Tool Plugins,本站所有转载文章系出于传递更多信息之目的,且明确注明来源,不希望被转载的媒体或个人可与我们联系,我们将立即进行删除处理。
相关研发服务和供应服务
相关推荐
KEYSIGHT示波器选型表
KEYSIGHT示波器选型,高清晰度示波器、混合信号示波器、手持式示波器等,最大存储器深度120kpts-2Gpts。
|
产品型号
|
品类
|
描述
|
宽带(MHz、GHz、GBd)
|
最大存储器深度(kpts、Mpts、Gpts)
|
最大采样率(GSa/s、KHz)
|
操作系统
|
类型
|
|
DSAZ504A
|
示波器
|
Infiniium 示波器:50 GHz
|
50 GHz
|
2 Gpts
|
160 GSa/s
|
Windows 10
|
Real-Time
|
选型表 - KEYSIGHT 立即选型
KEYSIGHT数字万用表选型表
KEYSIGHT数字万用表选型,手持式数字万用表、USB 模块化数字万用表、手持式钳形表等,基本 1 年 DCV 精度0.00%-0.5%。
|
产品型号
|
品类
|
描述
|
Digits of Resolution
|
基本 1 年 DCV 精度
|
连通性
|
测量功能
|
|
34470A
|
数字万用表
|
数字万用表,七位半,Truevolt DMM
|
7 ½
|
0.0016%
|
LAN,USB,GPIB (optional)
|
DCV and ACV,DCI and ACI,2- and 4-wire Resistance,Frequency,Capacitance,Diode test,Continuity test,Temperature
|
选型表 - KEYSIGHT 立即选型
如何把KEYSIGHT示波器连接到matlab上?
怎么把KEYSIGHT示波器连接到matlab上呢?本文将讲解详细步骤。
Keysight解决方案选择矩阵完全支持您的Keysight解决方案
描述- KeysightCare解决方案提供全面支持,旨在帮助用户解决技术难题,优化工作流程。服务包括硬件和软件的集成支持,旨在提高市场投放速度,减少计划外停机和项目延误。服务分为基本和高级两个层次,提供快速响应、现场技术支持、软件更新和预防性维护等。
Keysight i3070 09.20pc软件修补程序
描述- Keysight Technologies发布了一款针对i3070测试系统的软件补丁,版本号为09.20pc,发布日期为2018年11月。该补丁适用于装有i3070 09.20p软件的测试系统或工作站,支持Windows 7或Windows 10操作系统。补丁主要解决了多个变更请求,包括改进故障显示、电容补偿、用户界面布局、IPG功能、错误消息、安全性和其他功能增强。安装补丁时需以管理员身份登录,并遵循屏幕上的安装说明。安装后,用户可以通过Korn Shell窗口检查软件版本。
Keysight Joins White House Initiative to Improve IoT Security
By using the Keysight IoT Security Assessment, device designers and manufacturers can mitigate potential security issues. The solution automates the testing and validation process to reduce costs while speeding up time-to-market.
Keysight D9010CAUC CAUI-4测试应用程序
描述- 该资料详细介绍了Keysight D9010CAUC CAUI-4测试应用的使用方法,包括安装测试应用和许可证、准备测量、配置测试应用、配置开关矩阵、配置信号路径、进行测量和生成报告等步骤。资料涵盖了测试应用的硬件和软件要求、测试流程、测试参数配置、结果分析和报告生成等内容。
型号- D9010CAUC
Keysight Enables Microamp Solutions to Accelerate Development of mmWave Radio Units for Private 5G Networks
Keysight Technologies announced that Microamp Solutions has selected Keysight Open Radio Architect (KORA) solutions to meet increasing demand for mmWave radio units in private 5G networks.
Keysight 85024A高频探头
描述- 本指南为Keysight 85024A高频探头提供了用户和服务指南,包括产品描述、规格特性、安装、操作、性能测试和维护信息。指南强调了静电放电(ESD)防护的重要性,并提供了操作前的注意事项和操作说明。此外,还包括了探头的性能测试方法和维护信息,以确保探头满足其保证的规格。
型号- 85054B,85024A-001,11881-60001,11524A,08405-40003,85024-60013,85024-60014,11880-60001,85024-60015,85024-60016,1250-1477,5060-0549,8710-1806,85024A,41800-61672,11881-20007,10229A,85024-63071
Keysight 11683A量程校准器
描述- 本手册为Keysight 11683A量程校准器提供了操作和维护指南。内容包括校准器的基本信息、安装步骤、操作说明、维护指南以及安全注意事项。手册详细介绍了校准器的功能、操作方法、性能测试、调整和维护程序,旨在帮助用户正确使用和保养该设备。
型号- A2C1,5000,A2CR1-4,A2S1. A2R3,3455A,A3A1U1,1551A,A3A1QL,N1913A,A1,A2,436A,A3,34410A,A2U1,1801A,1314A,1821A,3000 X,A3A1U1A2,A3A1C6,A3A1C3,A3J1,A3A1C1,180C,A2R1,34461A,A3A,A2R2,A3R1,L4411A,34401A,34411A,435A,34465A,A3A1Q1,11683A,A3A1,A2C2
PCN-Keysight
型号- U1281A/R-50C-011-5,U1281A/R-50C-011-3,U1231A/R-50C-011-3,U1272A,U1231A/R-50C-011-5,U1212A/R-50C-011-3,U1212A/R-50C-011-5,U1273A/R-50C-021-5,N4433A/R-50C-016-3,U1273A/R-50C-021-3,U1252B/R-50C-011-5,U1233A/R-50C-011-5,U1232A,U1252B,U1115A,U1233A/R-50C-011-3,U1252B/R-50C-011-3,U1212A,U1273AX,U1241C/R-50C-011-3,U1241C,U1242C/R-50C-011-3,U1281A,U1242C/R-50C-011-5,U1241C/R-50C-011-5,U1273AX/R-50C-016-3,U1242B/R-50C-011-MU-5,U1253B/R-50C-021-5,U1242B/R-50C-011-MU-3,U1273AX/R-50C-016-5,U1253B/R-50C-021-3,U1251B/R-50C-021-5,U1232A/DST,U1241B/R-50C-011-5,U1242B/R-50C-011-3,U1241B/R-50C-011-3,U1242B/R-50C-011-5,U1241B,U1273A,U1253B,U1252B/R-50C-021-3,U1213A,U1177A/AB0,U1251B/R-50C-021-3,U1252B/R-50C-021-5,U1233A,U1177A/AB2,U1282A/R-50C-011-3,U1282A/R-50C-011-5,U1282A,U1213A/R-50C-011-3,U1272A/R-50C-021-5,U1213A/R-50C-011-5,U1211A/R-50C-011-3,N4433A/R-50C-011-3,U1273AX/R-50C-021-3,U1272A/R-50C-021-3,N4433A/R-50C-011-5,U1211A/R-50C-011-5,U1253B/R-50C-011-5,U1251B/R-50C-011-5,U1253B/R-50C-011-3,U1252B/R-50C-016-3,U1117A,U1273AX/R-50C-021-5,U1252B/R-50C-016-5,U1232A/R-50C-011-5,U1242C,U1242B,N4433A,U1232A/R-50C-011-3,U1251B/R-50C-011-3,U1231A/DST,U1273A/R-50C-011-5,U1271A/R-50C-011-5,U1253B/DST,U1271A,U1272A/R-50C-011-5,U1251B,U1271A/R-50C-011-3,N4433A/R-50C-021-3,33210U,N4433A/R-50C-021-5,U1272A/R-50C-011-3,U1273A/R-50C-011-3,N4433A/R-50C-016-5,U1118A,U1273AX/R-50C-011-MU-3,U1273AX/R-50C-011-3,U1273AX/R-50C-011-5,U1273AX/R-50C-011-MU-5,U1231A,U1252B/R-50C-011-MU-3,U1252B/R-50C-011-MU-5,U1211A
Keysight M9260A PXIe音频分析仪
描述- 本指南为Keysight M9260A PXIe音频分析仪的启动指南,内容包括安全注意事项、环境条件、法规信息、模块检查、安装和验证步骤。指南详细介绍了模块的拆箱、检查、安装控制器和软件、模块安装、操作验证等过程,旨在帮助用户正确使用和维护M9260A音频分析仪。
型号- M9260A
Keysight E5071C ENA网络分析仪
描述- 本资料为Keysight E5071C ENA系列射频网络分析仪的服务指南,内容涵盖安全注意事项、性能测试、故障排除、可更换部件和更换程序。指南详细说明了仪器的操作、维护和维修过程,包括安全操作、性能测试方法、故障诊断和解决步骤,以及如何更换仪器的各个组件。
型号- 8491A,11713B,1250-1811,11713A,85032-60015,8491C,E5070-65071,8491B,85032F,85052D,E4413A,8710-1764,33250A,3458A,1251-2277,909F,8496G-H60,85052-60007,Z5623A-K01,85052-60006,9135 -5852,85033E,E5071C ENA,53151A,53131A,8482A,8496G-001,5071A,N1914A,34411A,N6314A,11683A,N8482A,33120A,85054D,11901B,85050D,1250-0781,1250-0780,E9304A,E4419A,34410A,8120-8862,53132A,33220A,Z5623A,85027-60005,8120-1839,1250-1745,1250-2879,11512A,53181A,8496G,11730A,1250-1744,34401A,1250-0929,8120-1840,85032-60016,85032-60018,8120-8319
Keysight Cyber Training Simulator Provides Universities a Realistic Turnkey Cyber Range
Keysight Technologies has introduced Keysight Cyber Training Simulator (KCTS), a comprehensive, turnkey cyber range that simulates real-world traffic using the company‘s BreakingPoint solution.
现货市场
服务
支持 3Hz ~ 26.5GHz射频信号中心频率测试;9kHz ~ 3GHz频率范围内Wi-SUN、lora、zigbee、ble和Sub-G 灵敏度测量与测试,天线阻抗测量与匹配电路调试服务。支持到场/视频直播测试,资深专家全程指导。
实验室地址: 深圳/苏州 提交需求>
提供是德(Keysight),罗德(R&S)测试测量仪器租赁服务,包括网络分析仪、无线通讯综测仪、信号发生器、频谱分析仪、信号分析仪、电源等仪器租赁服务;租赁费用按月计算,租赁价格按仪器配置而定。
提交需求>

































































































































































































登录 | 立即注册
提交评论