Security in IoT Devices: Challenges and Solutions


Anything connected to the internet is likely to face an attack at some point. Attackers may try to remotely compromise IoT devices to steal data, conduct DDoS attacks, or try to compromise the rest of the network. IoT security demands an integrated approach that covers the entire device lifecycle, from design and development to deployment and maintenance.
Security in IoT devices is a primary concern for customers and device manufacturers alike. To ensure secure communication between two devices, there are two key areas that need to be secured. The first is the pipe between the two devices and the data that flows within these channels. This is taken care of by communication protocols like Thread, Bluetooth, etc. The second is the security of the device itself, which is the responsibility of the developer.
There are several standards and frameworks that aim to provide guidelines and best practices for IoT security, such as the IoT Security Foundation, the NIST Cybersecurity Framework, the ISO/IEC 27000 series, and the OWASP IoT Top 10. However, there is no single universal standard that applies to all IoT devices, as different devices have different security requirements and challenges depending on their use cases, functionalities, and environments.
Therefore, IoT device manufacturers and developers need to adopt and implement the standards and frameworks most relevant and suitable for their specific devices and keep up with emerging trends and technologies in IoT security.
While security threats in IoT devices can be low-risk, others can be high-impact and cause considerable damage.
Let us take a dive into the most common IoT security threats.
Unauthorized Access
One of the most common security threats is Unauthorized access. Hackers can gain access to IoT devices through weak passwords and other vulnerabilities, allowing them to control the device or steal personal information. This can include accessing the device's camera or microphone or using the device to launch DDoS attacks.
Data Breaches
Another common security threat for IoT devices is data breaches, which occur when an attacker obtains sensitive or confidential data from the device or its network. This can compromise the privacy and integrity of the data and expose the device or the user to identity theft, fraud, or blackmail.
Malware Attacks
A third common security threat for IoT devices is malware attacks, where malware (normally malicious software) executes unauthorized actions on the victim's system, this can impair the functionality and reliability of the device, and cause damage, disruption, or sabotage to the device or its network.
Distributed Denial of Service Attacks
Another security threat for IoT devices is denial-of-service attacks, DDoS is an attack that targets the availability of resources and servers of a network by flooding the communication medium from distinct locations by using various IoT devices, which makes it harder to detect. Thus, analyzing and defending DDoS is a protruding field of research.
Physical Tampering
This is another threat that occurs when an attacker physically accesses, changes, or damages the device or its components. It can compromise the integrity, functionality, and confidentiality of IoT devices. This can affect the security and functionality of the device, and enable the attacker to access, manipulate, or destroy the device or its data.
How SILICON LABS Addresses IoT Security Challenges
When the subject of security comes up, there is generally a mention of data breaches, malware attacks, denial of service attacks, etc. However, there are some additional attacks that IoT devices are prone to. This can be as simple as an attacker attempting to run their unauthorized code on your device, or attempts to perform product counterfeiting, or complex like differential power analysis attacks.
Silicon Labs addresses these concerns through Secure Vault™. Secure Vault by Silicon Labs is an advanced suite of security features designed to protect Internet of Things (IoT) devices from such evolving threats.
Silicon Labs is a leading provider of silicon, software, and solutions for IoT devices, with a focus on delivering secure and reliable connectivity for a smarter, more connected world, offers a robust and comprehensive portfolio of IoT security products and services with features like secure boot, secure debug, secure key management, and secure identity.
Let us look at the prevalent security countermeasures that can help protect the end-device secret and private keys and ensure a completely secure ecosystem.
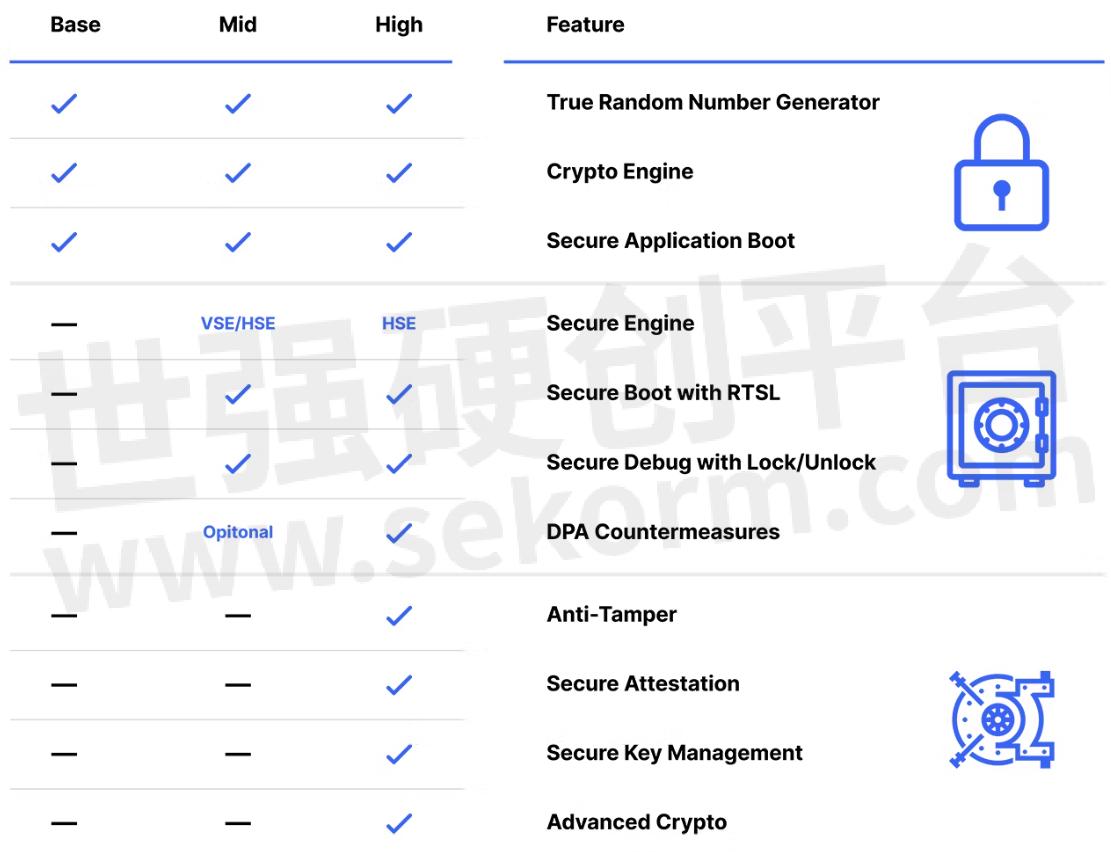
Secure Vault Mid features will protect end-devices from logical attack vectors. Applications that also require protection against physical attack vectors will require Secure Vault High features such as secure key management and tamper protection. Device manufacturers looking to protect their devices from product counterfeiting as well as cloning of devices should consider investing in secure identity, which enables commissioners to authenticate the identity of the device before allowing it to join the smart IoT network.
Secure Key Mmanagement
There are various methods for storing keys securely. One method is to create very expensive memory cells that are buried into a security subsystem. These memory cells are expensive from a silicon die area perspective, and there is always the important decision: How many do we put in the chip? Ultimately, there are never enough cells and some key material ends up being stored unencrypted in plaintext in standard memory. Another method for secure key storage is to use a Physically Unclonable Function, or a PUF, to create a device-specific Key Encryption Key and store all key material in encrypted Key BLOBs in standard memory. This has the additional benefit of giving you almost unlimited secure key storage.
Physically Unclonable Function (PUF)
A PUF is a physical structure embedded in an integrated circuit (IC) that is very hard to clone due to its unique micro- or nano-scale properties originating from inherent deep-submicron manufacturing process variations. The static random access memory (SRAM) PUF is the best-known PUF based on available standard components.
Other Attack Vectors
There is always a threat of an attacker attempting to run their unauthorized code on our device, Secure boot addresses this concern by validating the signature on the application code before allowing it to run on the device. This is based on a ROM-based Root of Trust that serves as a secure anchor for the verification sequence. We can also prevent unauthorized access to the device by locking the debug port and by enabling DPA countermeasures to protect the device from being unlocked through side-channel attacks.
Security is a very interesting aspect of IoT devices as one can never ensure 100% protection against it. Just like more layers make it difficult to peel an onion, the more layers we create in a device, the harder and more expensive it becomes for an attacker to access the information. We at Silicon Labs, follow a security-by-design philosophy, which means that security is embedded and integrated into every stage of the device lifecycle, from design and development to deployment and maintenance.
- |
- +1 赞 0
- 收藏
- 评论 0
本文由samsara转载自SILICON LABS Official Website,原文标题为:Security in IoT Devices: Challenges and Solutions,本站所有转载文章系出于传递更多信息之目的,且明确注明来源,不希望被转载的媒体或个人可与我们联系,我们将立即进行删除处理。
相关推荐
芯科科技深度解读边缘智能:高效机器学习平台、安全性、低功耗和无线连接缺一不可
芯科科技高级营销经理Matt Maupin先生在EEPW电子产品世界的物联网边缘智能(Edge Intelligence)专题访谈中进一步分析市场的前景、与云计算的关系、数据处理和分析的特殊要求等方面,并介绍芯科科技因应边缘智能的发展所提供的软硬件平台解决方案。
Wi-Fi 6 Module 802.11ax: Shaping the Future of Wireless
This article explores the numerous benefits of the Wi-Fi 6 Module, including faster speeds, increased capacity, and improved performance in crowded environments. Additionally, the article delves into the key features of the Wi-Fi 6 Module that set it apart from previous generations, such as improved power efficiency and better security measures.
The Distinguishing Differences Between 4G LTE Routers and Industrial 4G Routers
The distinguishing differences between 4g lte routers and industrial 4g routers lie in their design, performance, security, and additional features. While ordinary routers may suffice for basic consumer use, industrial 4g routers are the superior choice for industrial applications due to their resilience, high-performance capabilities, advanced security features, and tailored functionality.
芯科科技全新xG26系列记忆体容量和GPIO翻倍,扩展Matter开发支持
SILICON LABS宣布推出新的xG26系列无线片上系统(SoC)和微控制器(MCU),这是迄今为止物联网行业领先企业性能最高的系列产品。该新系列产品包括多协议MG26 SoC、低功耗蓝牙(Bluetooth LE)BG26 SoC和PG26 MCU。这三款产品的闪存和RAM容量都是芯科科技其他多协议产品的两倍,旨在满足未来物联网(IoT)的需求,以应对一些要求严苛的新兴应用,如Matter。
完美结合无线连接、人工智能和安全性的智能家居解决方案
智能家居应用正在快速发展,其中推动智能设备的发展关键因素在于易于使用,而实现这一目标的最佳方法,便是让设备通过人工智能和机器学习技术进行自我思考。本文将为您介绍人工智能将如何强化智能家居设备的功能,以及由芯科科技(Silicon Labs)所推出的解决方案,将如何增强智能家居设备的功能性与安全性。
NiceRF Launched Low Power Multi Sensor Monitoring Node IOT-N010, Mainly Used for Sensor Monitoring and Control of the Internet of Things
This paper mainly introduces the new product of Low Power Multi Sensor Monitoring Node IOT-N010 launched by G-NiceRF, and introduces the features and application scenarios.
Unlocking Wireless Home Security Capabilities with Wyze Lock Bolt smart door lock that is based on Silicon Labs’EFR32MG21 2.4GHz Wireless SoC
Wyze Lock Bolt smart door lock uses Silicon Labs’ EFR32MG21, a 2.4GHz wireless SoC optimized for Zigbee applications, which features an integrated security subsystem and is designed to increase processing capability, improve RF performance, and lower active current.
Quectel EG91-EX LTE Cat 1 Module Receives EU RED Cybersecurity Certification
Quectel EG91-EX LTE Cat 1 module has been awarded the EU Type Examination Certificate for RED Cybersecurity. This certification confirms that the module complies with the cybersecurity requirements outlined in RED DA, providing Quectel customers with assurance in the module’s robust cybersecurity features.
Kinghelm Passive RFID Tag KH-RFID-20-BQ Features High Efficiency Read/Write, Precise Identification, Security and Reliability
KH-RFID-20-BQ is a 20mm diameter RFID tag operating at a frequency of 13.56MHz, classified under passive RFID tags. Passive RFID tags do not require an internal battery; instead, they operate by receiving RF signals from RFID readers, offering long lifespan, low cost, and convenience. The KH-RFID-20-BQ tag utilizes advanced chip technology and optimized antenna design to ensure stable and reliable read/write performance in various environments.
Silicon Labs xG26 Sets New Standard in Multiprotocol Wireless Device Performance
Silicon Labs today announced their new xG26 family of Wireless SoCs and MCUs, the IoT industry leader‘s highest performance device family to date. The new family consists of the multiprotocol MG26 SoC, the Bluetooth LE BG26 SoC, and the PG26 MCU.
ATP Introduces High-Endurance M.2 2230 SSDs Packed with Customizable Security Features
ATP ELECTRONICS introduces its latest 3D triple-level cell (TLC) flash storage solid state drives (SSDs): the N700 and N600 Series, which offer hardware-based security features, such as Write Protection and Quick Erase, by project and customer request.
EFR32BG22 Wireless SoC Enables IoT Devices to Operate 10+ Years on 1 Conin Cell Battery | Silicon Labs
Equipped with an Arm® Cortex®-M33 core, BG22 SoCs achieve extremely low power levels while in an operational sleep state down to 1.4 µA. These devices are Bluetooth 5.2 compliant, support direction finding and low-power Bluetooth mesh networks and integrate enhanced security features such as Secure Boot with Root of Trust (RTSL).
蓝牙安全功能手册–90分钟
描述- 本资料通过实验室实践,展示了蓝牙安全特性在实际应用中的使用,包括GATT权限和配对过程。内容涵盖GATT权限的运用、不同配对过程的演示以及GATT和安全管理器设置的代码示例。实验涉及不同配对方法(如“即插即用”、“输入配对密钥”和“数字比较”)对安全特性的影响,并提供了相应的代码片段和配置说明。资料还介绍了GATT权限的定义、认证、加密以及服务与特性的发现过程。
Silicon Labs Helping Smart Home Manufacturers Meet IoT Security Regulations
Silicon Labs is committed to leading the way in IoT security. Secure Vault™, Silicon Labs’industry-leading security suite, defends against both widespread software attacks and emerging hardware threats, thoroughly passing independent lab tests simulating real-world assaults.
电子商城
品牌:SILICON LABS
品类:Wireless Gecko SoC
价格:¥8.1764
现货: 101,879
品牌:SILICON LABS
品类:Mighty Gecko Multi-Protocol Wireless SoC
价格:¥27.0929
现货: 90,767
品牌:SILICON LABS
品类:Wireless Gecko SoC
价格:¥10.4994
现货: 50,699
现货市场
品牌:SILICON LABS
品类:Switch Hall Effect Magnetic Position Sensor
价格:¥2.2924
现货:126,000

































































































































































































登录 | 立即注册
提交评论