Microsoft Exchange Server EWS Insecure Deserialization, Leverage Subscription Service to Stay Ahead of Attacks




With the recent events, there have been speculations regarding increasing cybersecurity attacks on organizations by the threat actors. Amidst the speculations, name of a CVE which has popped up is CVE-2020-17144 which is a Remote Code Execution (RCE) vulnerability in Microsoft Exchange Server 2010 SP3.
What is Microsoft Exchange
Microsoft Exchange is a mail and calendaring server implemented using ASP.NET. Microsoft Exchange Server provides web access for Exchange Web Services (EWS) which is an application program interface (API) that allows programmers to access Microsoft Exchange items such as calendars, contacts, and email.
Vulnerability Details
This CVE affects all the versions of Microsoft Exchange 2010 SP3 till Cumulative Update (CU) 30 (released on 08.12.2020). There is a Proof of Concept (PoC) publicly available on Github. We will test out the PoC on a test machine in a moment. Before we do that, here is a brief, simplified explanation of the root cause of the vulnerability - EWS uses SOAP (Simple Object Access Protocol) messages, which are XML based to access and modify the user configuration object. One of the methods (CreateUserConfiguration) accepting SOAP messages has a field called "binary data" which accepts serialized data. This serialized data is de-serialized on the server side without any validation. So, an authenticated attacker can embed malicious data in these SOAP messages capable of performing RCE causing the vulnerability.
Attack in action
1. Configuring the target
Firstly, we need a Windows OS which supports deployment of Microsoft Exchange Server. For that we deploy a Windows Server 2012 VM. We can get one evaluation ISO from here.
We will use the same VM to launch the attack too. We can use some other machine on the same network as well.
Active Directory (AD) Domain needs to be deployed on this machine. We can follow the guide from one of my previous blogs in the 'Deploying the Domain Controller' section.
After deploying an AD, we need to install the Microsoft Exchange Server 2010 SP3.
The version downloaded won't have any Cumulative Update installed. Visual Studio C++13 is needed if we want to apply the latest vulnerable Cumulative Update 30 over it.
Next, we need to the deploy the MS Exchange server 2010, we can follow the tutorial here.
Once the Exchange setup done, we need to make sure we can login to the following URLs by visiting them in the browser - https://localhost/owa and https://localhost/EWS/exchnage.asmx
Optional: We can disable SSL for EWS to see what's being exchanged in the wire in plain text. To monitor we need to download a network monitoring tool like Wireshark.
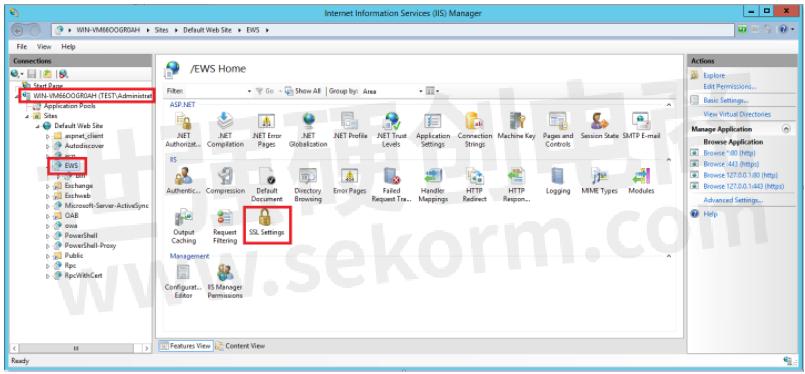
To disable SSL, search for IIS manager and go to the SSL settings of EWS and remove the check on the Require SSL option.
2. Preparing the payload
We download the Public PoC available online and navigate to it inside Command Prompt.
The payload needs to be compiled, but before compiling, if SSL has been disabled for EWS, open the CVE-2020-17144.cs file in a text editor and replace the word https to http.
Now in command prompt, run the batch script called make. This should create the CVE-2020-17144 file which is our payload.
3. Executing the Payload
To give an idea of what the payload is designed to do is, it creates a serialized object, which hosts a malicious server/webpage on the server, which can respond to user query by executing the commands that is supplied, whoami in this case.
Now, to launch the attack, run -
CVE-2020-17144 <ip_address> <username> <password>
Replace the IP address, username, and password with corresponding details
This should return successfully with message 'User Configuration Created', which means the attack probably has been successful.
To test if the attack was successful -
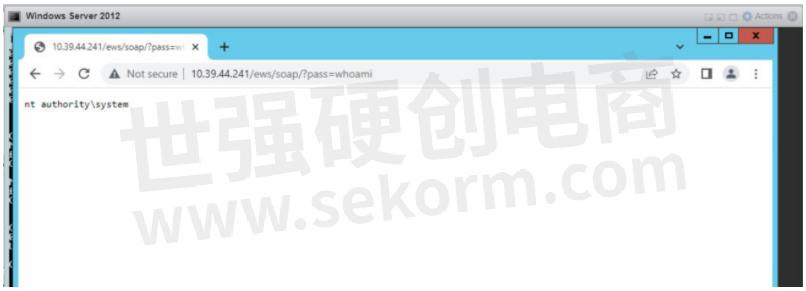
Visit http://10.39.44.241/ews/soap/?pass=whoami in the browser
This should return the username which means command execution was successful
We have also tested it to be working on Exchange Server 2010 SP3 with Cumulative Update 30.
Traffic on the Wire
While we executed the payload, we used Wireshark to monitor the packets exchanged over the network.
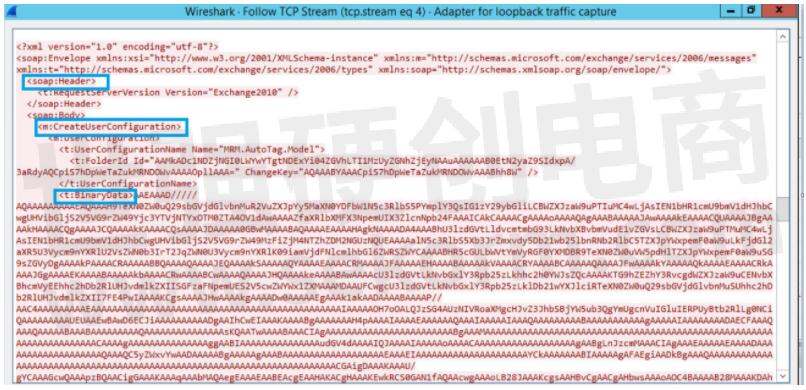
We notice a few things that we discussed while talking about the reason of the vulnerability to be true here.
We see the payload being delivered using SOAP messages.
We see the XML tag CreateUserConfiguration indicating the usage of vulnerable function.
We also see the XML tag binary data containing the malicious serialized payload Base64 encoded.
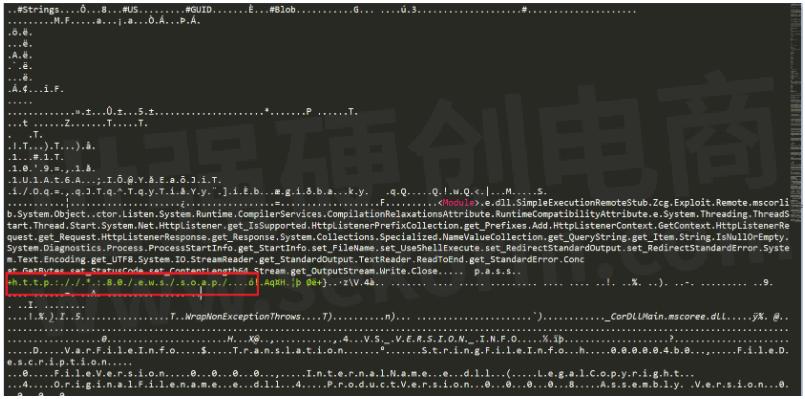
If we base64 decode the payload, we can see some info like the URL where the payload will start the server, which we used to verify the attack has worked.
Mitigation
To be able to mitigate this attack, make sure to apply the latest Cumulative Updates, at least CU 31 to the vulnerable Microsoft Exchange 2010 server.
You can also use KEYSIGHT test platforms with ATI subscription to be able to safeguard your network against such attacks. Keysight Threat Simulator or BreakingPoint products can help you assess your network security controls and determine whether you can be protected prior to patch. This kind of assessment is valuable as it can let you know if you have protection during the time before a change management window will open.
Leverage subscription service to stay ahead of attacks
Keysight's Application and Threat Intelligence (ATI) Subscription provides daily malware and bi-weekly updates of the latest application protocols and vulnerabilities for use with Keysight test platforms. The ATI Research Center continuously monitors threats as they appear in the wild and has just released a strike for this CVE as part of BreakingPoint System's recent update 2022-05.
The following image shows a screenshot of this CVE as a strike in BreakingPoint System.
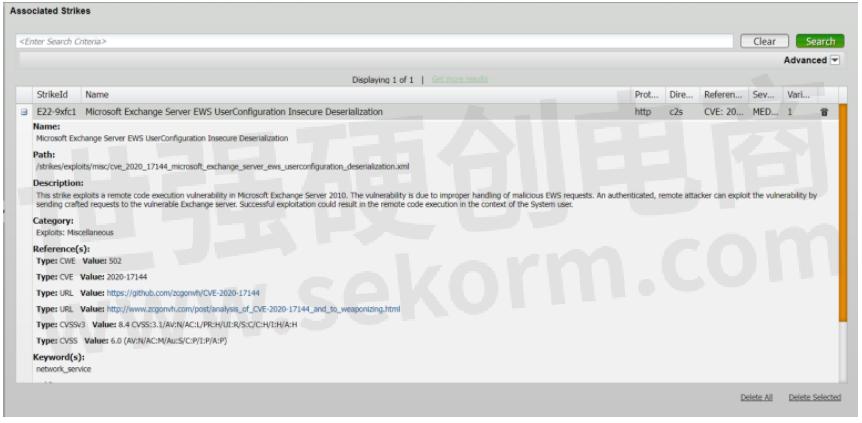
Customers of BreakingPoint now have access to attack campaigns for different advanced persistent threats, allowing them to test their currently deployed security controls' ability to detect or block such attacks.
- |
- +1 赞 0
- 收藏
- 评论 0
本文由董慧转载自Keysight,原文标题为:CVE-2020-17144 : Microsoft Exchange Server EWS Insecure Deserialization,本站所有转载文章系出于传递更多信息之目的,且明确注明来源,不希望被转载的媒体或个人可与我们联系,我们将立即进行删除处理。
相关研发服务和供应服务
相关推荐
Keysight and ETS-Lindgren Deliver First Narrowband Non-Terrestrial Networks Over-The-Air Test Solution
Keysight and ETS-Lindgren announce an industry-first OTA test solution for devices supporting the NB-NTN technology. The combined solution comprises Keysight‘s UXM E7515B NTN software and ETS-Lindgren‘s OTA test chambers and EMQuest Antenna Measurement Software.
Keysight Enables Samsung to Establish 5G Data Call Based on 3GPP Release 16 Specifications
Keysight Technologies announced that Samsung Electronics‘ System LSI Business has selected the company‘s 5G test platforms to establish a 5G data call based on 3GPP release 16 (Rel-16) specifications on June 14, 2021. Samsung selected Keysight‘s 5G network emulation solutions to successfully demonstrate a data link based on 3GPP Rel-16 specifications for the 5G new radio (NR) standard. Samsung used Keysight‘s 5G Protocol R&D Toolset and Test Application software to validate the modem maker‘s Exynos Modem chipset, which many global device makers use to bring 5G products to market.
Keysight Supports Verification of Open RAN Radio Units Powered by Qualcomm Infrastructure Solutions
This validation enables Open RAN Radio Unit (O-RU) and gNodeB (gNB) vendors to verify products using the Qualcomm® 5G RAN Platforms throughout the design and production workflow.
Keysight支持协议:汽车功能测试、在线测试和成像检测平台的耗材排除清单
型号- N7280-27965,E4000-66220,E7200-22402,2110-1074,5186-2385,5186-2540,5186-2387,5186-2420,5186-6109,5060-0418,0490-1727,E6170-22100,2110-0665,0490-1688,0490-1320,1990-3511,5186-2435,03066-24703,2110-1002,03066-24704,N7200-27965,2110-1009,2110-0713,6040-1349,0100-0829,2110-1011,E7200-67971,0490-1828,E1418-66704,0490-0615,3140-1060,03066-61300,2110-0969,03066-61302,03066-63600,0890-1832,2110-0051,2110-1022,2110-0055,0490-1839,N7210-27965,2110-0699,03066-21212,5186-2744,1990-3607,1990-3608,5186-4929,5186-1816,5186-4928,1990-3606,N7280-27802,1252-8421,5186-4404,5186-2501,2110-0587,3131-0675,0490-1804,2110-0623,2110-0907,5186-2238,5186-4934,0490-2064,0490-2063,03066-67908,1250-0076,N7200-27803,5186-1662,5186-2512,0490-1814,03066-67910,5186-3041,5186-2196,0490-1774,1400-0051,44265-80004,6040-0970,0490-1772,5186-2964,0100-1678,44902-60000,2140-0592,2140-0593,5186-1593,5186-4348,2110-1332,2110-0003,N7200-37702,0490-2798,0490-1587,0960-2134,1990-1876,5186-5280,5186-5281,1990-2201,E7200-27965,0101-1259,1500-1021,8710-1857,03066-26701
ARESONE-S-400GE QSFP-DD高密度8端口测试系统数据表
型号- QSFP-DD-MPO16-CBL,S400GD-8PHW-4P,944-1240,S400GD-8PHW-8P-QDD,T400GDR-4P-QDD,VISION X,948-0061,991-0151,QSFP-DD-SR8-XCVR,991-0147,991-0148,S400GDR-8PHW-4P-QDD,944-1170-06,942-0140,942-0142,930-2204,T400GP-4P-QDD,944-1232,930-2203,905-1058,930-2202,905-1059,S400GD-4P,930-2201,930-2207,930-2206,S-400GE QSFP-DD,930-2205,944-1231,QSFP28-PSM4-XCVR,948-0076,S400GDR-8PHW-4P,948-0073,930-2200,948-0072,QSFP-PLUS-PLR4-XCVR,930-6001,QSFP-DD-CWDM4-XCVR,SFP28-LR-XCVR,S400GDR-8P-QDD,M7300-12PC,T400GD-4P-OSFP,QSFP28-SR4-XCVR,S400GDR-8P,942-0151,944-1173-05,942-0152,QSFP-DD-R400GE,944-1300,944-1301,T400GD-4P-QDD,944-1302,944-1303,944-1304,944-1305,942-0125,942-0124,K400 QSFP-DD-400GE,QSFPDD2XQ56-2-5M-CBL,S400GDR-16PHW-16P-QDD,942-0088,S400GD-8PHW,MVX-NS12PC,QSFP-DD-2-5M-CBL,T400GDR-4P-OSFP,QSFP-QDD,S400GD-16PHW-8P-QDD,942-0090,QSFPDD4XQ56-1-5M-CBL,QSFP-DD-FR4-XCVR,QSFPDD8XQ56-1-5M-CBL,942-0138,942-0139,995-8036,942-0096,942-0093,944-1171-06,942-0094,MVX-PS8PC,947-4058,947-4059,VISION 7303,VISION 7300,944-1164,T400GD-8P-OSFP,930-3461,QSFP-DD-1M-CBL,SFP28-SR-XCVR,QSFP-DD-SR8-CBL,QSFP-DD800,QSFP28-SFP28-ADPT,QSFP-DD-2M-CBL,BD-7816AC-32PC,942-0068,905-1080,905-1081,942-0106,905-1082,905-1083,905-1084,905-1085,905-1086,905-1087,942-0067,BD-7816DC-32PC,QSFP-DD 400GE,S400GDR-8PHW-8P-QDD,S400GDR-8PHW-8P,944-1152,944-1153,S400GD-8P,QSFP-DD-DR4-CBL,T400GDR-8P-QDD,948-0038,942-0079,948-0037,948-0036,942-0071,S400GDR-16PHW-8P-QDD,942-0110,QSFPDD-4XQ28-AEC-CBL,VISION X FAMILY,905-1098,905-1099,400G-ZR,991-2030,QSFP28-LR4-XCVR,944-1186,944-1187,948-0040,991-2032,QSFP28-PSM4-CBL,991-2033,S400GD-8PHW-4P-QDD,S400GD-16PHW-16P-QDD,K400 QSFP-DD-R400GE,944-1172-05,VISION E100,944-1177,944-1178,QSFP-PLR4-XCVR,S400GD-8PHW-4P-QDQ,944-1173,T400GD-8P-QDD,944-1174,944-1175,944-1176,QSFP-DD-DR4-XCVR,948-0051,S400GD-16P-QDD,S400GD-8P-QDD,QSFP-DD-LR4-XCVR,QSFP28-CWDM4-XCVR,QSFP28-DR1-XCVR,948-0059,QSFP-PLR4-CBL,T400GDR-8P-OSFP,948-0055,944-1170,944-1171,QSFP-DD,944-1172,400GBASE-CR8,992-0072
Keysight(是德科技)台式仪器和系统开关产品选型指南
目录- Data Acquisition/Data Switch System Multifunction Switch/Multifunction Measure Unit LXI Switching/LXI Control USB Switching/USB Data Acquisition 3499 Switch PXI Switch Modules VXI Switches Electromechanical Switches Solid State Switches Switch Drivers RF Switch Platforms Custom Switch Solutions
型号- 44473A,M9121A,N2268A,M9133A,N2272A,N2260A,U9397C,U9397A,34921A,34945A,E1460A,34933A,E1472A,34905A,L4490A,E1468A,L4450A,E1347A,N2267A,44472A,M9122A,M9146A,L4433A,L4445A,34945EXT,L4421A,34932A,E1364A,E1473A,E1352A,34904A,N2266A,M9187A,E8480A,M9147A,P9400C,P9400A,U2356A,U9400C,34931A,E1474A,U9400A,U2121,34903A,34939A,L4452A,M9150A,44474B,M9152A,44474A,44474C,M9148A,U2331A,U2751A,34970A,U2355A,E1366A,E1475A,34942A,E1463A,L4491A,34902A,34938A,L4451A,M9151A,11713B,M9153A,11713C,M9101A,N2276A,N2264A,U2354A,M9149A,E1370A,P9402C,P9402A,E8462A,34941A,E1476A,34925A,34937A,E1339A,85331B,M9130A,U2802A,N2263A,L4490,M9102A,U2353A,34980A,E1368A,34952A,E1465A,L4437A,34924A,44476B,34908A,44476A,85332B,M9131A,44471A,N2262A,M9103A,44471D,M9018A,U2352A,P9404C,E8460A,P9404A,E1466A,E1345A,E1442A,34951A,34923A,34947A,34959A,34907A,E1369A,M9120A,M9132A,44470A,44470D,M9128A,N2261A,U2351A,34950A,E1467A,34934A,34922A,34946A,44478B,34906A,44478A
Keysight and Samsung to Demonstrate 5G Non-Terrestrial Networks Data Connection at Mobile World Congress 2023
Samsung has been at the forefront of 5G modem technology and with Keysight‘s emulators and test platforms, we are able to quickly develop and evaluate 5G NTN connections using our Exynos Modem development platform.
Keysight‘s Take on CVE-2022-30190 MSDT Follina Exploit
MSDT RCE vulnerability has taken the internet by storm with it being still a zero-day. Keysight‘s ATI Research Centre continuously checks threats.
S8702A射频自动化工具集技术概述
型号- E7515E,M1740A,C8702000A,E7515B,C870200AA,S8702A,E7770A,C870250AA,C870250BA,C870250CA
Keysight‘s 2021 Internet Application Trends
Keysight‘s Application and Threat Intelligence (ATI) Subscription provides daily malware and bi-weekly updates of the latest application protocols and vulnerabilities for use with Keysight test platforms.
S8702A 5G射频自动化工具集
描述- Keysight的5G射频自动化工具集利用E7515B或E7515E UXM 5G无线测试平台,为用户提供全面测试,快速验证5G新无线(NR)设备的发射(Tx)和接收(Rx)性能,符合3GPP规范。该工具集是Keysight 5G网络仿真解决方案套件的一部分,提供灵活且易于使用的软件环境。工具集支持非独立(NSA)和独立(SA)两种5G部署模式,并提供一系列自动化测试功能,以优化测试时间和性能验证。
型号- E7515E,C8702000A,E7515B,S8702A,C870250AA
Keysight Enables Xiaomi to Accelerate 5G Release 16 Device Validation
Keysight Technologies announced that Xiaomi has selected Keysight‘s 5G device test solutions to accelerate 5G Release 16 (Rel-16) device validation in support of the latest 3GPP 5G new radio (NR) features and specifications.
Keysight‘s Take on Spring4Shell
Keysight‘s Application and Threat Intelligence (ATI) Subscription provides daily malware and bi-weekly updates of the latest application protocols and vulnerabilities for use with Keysight test platforms. The ATI Research Center continuously checks threats as they appear in the wild and has released a strike for both the CVEs as part of BreakingPoint System’s recent update 2022-07 (CVE-2022-22963) and 2022-08 (CVE-2022-22965) with multiple variations of the attack to help keep your network secure. More information is present here.
结合协议分析和流量生成测试平台的新兴测试解决方案白皮书
描述- 本文探讨了存储区域网络(SAN)测试平台的发展,分析了传统测试环境的挑战,如可扩展性、灾难模拟、测量和成本问题。文章介绍了新兴的测试解决方案,包括SAN测试平台、被动监控工具和流量干扰器,以及多功能测试平台,旨在提高测试效率和降低成本。此外,文章还强调了Agilent Technologies在测试和测量支持、服务和协助方面的承诺。
Keysight First to Enable Laptop Vendors to Verify Arm-based 5G PCs Powered by Windows on Snapdragon Compute Platforms
Keysight Technologies, Inc. is first to enable laptop vendors to verify Arm-based 5G personal computers (PCs) powered by Windows on Snapdragon® Compute Platforms with integrated software-centric test solutions.
现货市场
服务
提供是德(Keysight),罗德(R&S)测试测量仪器租赁服务,包括网络分析仪、无线通讯综测仪、信号发生器、频谱分析仪、信号分析仪、电源等仪器租赁服务;租赁费用按月计算,租赁价格按仪器配置而定。
提交需求>
朗能泛亚提供是德(Keysight),罗德(R&S)等品牌的测试测量仪器维修服务,包括网络分析仪、无线通讯综测仪、信号发生器、频谱分析仪、信号分析仪、电源等仪器维修,支持一台仪器即可维修。
提交需求>






































































































































































































登录 | 立即注册
提交评论